For instance, your Facebook posts are unindexed and won’t be found via a web browser. Your email inbox, online banking and Google Drive folders are undiscoverable via a web browser. It’s the parts of your internet activity that aren’t hidden per se, but can’t be accessed by others online.
- In this setup, the VPN connection acts as a middle layer between your device and Tor, routing your internet traffic through the VPN before it reaches the Tor network.
- It’s essential to understand that criminal intent lies with the individuals and not the tools they use.
- Law enforcement agencies keep an ear to the ground on the dark web looking for stolen data from recent security breaches that might lead to a trail to the perpetrators.
- If you have heard your peers or colleagues throw this term around and are wondering, “What is the dark web?
- By utilizing advanced threat detection, real-time monitoring, and a multi-layered approach, EDR safeguards personal data and prevents sophisticated cyber attacks.
Secure Your Connection
Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web). It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource. Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public.
The browser is available for Linux, macOS, and Windows desktop and laptop computers. A Tor Browser from the Tor Project is available for Android, and The Onion Browser from developer and journalist Mike Tigas is available for iOS mobile devices, which the Tor Project links to. This information can be used to target ads and monitor your internet usage. In combination with that data, and data gathered by other methods and/or tactics may in fact lead to complete exposure and could eventually lead to the police standing at your doorstep.

The darknet is a private place where nobody can intercept, monitor, or steal anything online from you. The Tor Browser works by routing internet traffic through a global network of server nodes to mask your IP address and activity. It encrypts data multiple times, each layer peeled off by a different node, helping to enhance user privacy and making tracking or surveillance extremely difficult. You’ll need a specialized dark web browser like Tor, which lets you access hidden parts of the internet while protecting your identity.

Verify onion URLs
Research what they offer and assess your privacy needs to make a decision about which dark web browser works best for you. Due to certain requirements from Apple, Tor Browser is not available for iPhones, but there are still ways you can connect to the Tor network when using an iOS device. Unlike Tails, Whonix is built for everyday use and comes with all the major productivity apps, including a word processor and an email client. If you are up for a challenge, you could try combining Whonix with the Qubes hypervisor (like Edward Snowden does).
ChatGPT’s Next Phase: AI-Powered Ad Platform To Transform Digital Advertising And Revenue Streams
Additionally, some users on the dark web may attempt phishing scams to steal personal information and extort victims. On the dark web, you’re expected to find illegal and prescription drugs (including Marijuana). Also, some toxic chemicals are peddled on the dark web that may cause severe damage to the targets. The deep and dark webs seem like illegal places you should not visit.
Browse Privately

This has increased the risk for dark web operators mishandling personal data. Explore the legal nuances of accessing the dark web, including potential penalties and jurisdictional differences. Tor Browser masks your IP address and routes traffic through multiple servers. Many cybercriminals operating on the dark web have been arrested by law enforcement agencies, proving that anonymity isn’t foolproof.
Tor-Enabled OS Alternatives To Tails For Secure Dark Web Browsing
It contains millions of scientific research documents from around the world. The site seeks to liberate information by making it free to individuals and institutions. People search sites can help locate your old lost friend or if you want to know something about some…
Use A VPN To Stay Safer On The Dark Web
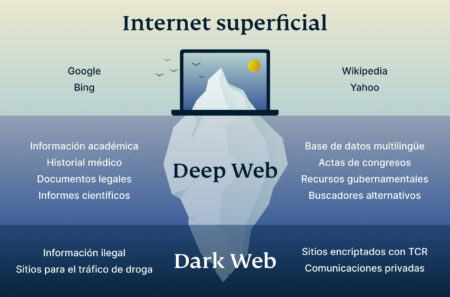
The terms “deep web” and “dark web” are sometimes used interchangeably, but they are not the same. Deep web refers to anything on the internet that is not indexed by and, therefore, accessible via a search engine like Google. Deep web content includes anything behind a paywall or requires sign-in credentials. It also includes any content that its owners have blocked web crawlers from indexing.

The dark web is a murky part of the internet that isn’t accessible via a normal browser — and can be dangerous to visit if you don’t know what you’re doing. We’ll show you how to access and browse dark web sites, and how using a VPN to encrypt your connection can help you visit the dark web more securely. This part of the internet is notorious for illegal activities, facilitated by the anonymity it offers.
- Legal uses include forums for free speech and privacy, while illegal activities may involve the sale of drugs, weapons, or stolen data.
- However, it’s important to note that while Tor provides anonymity, it does not guarantee security.
- You can inadvertently download malicious software by visiting these websites, infecting your system.
- However, Bitcoin’s relevance in the digital world has also made it a scam target.
Click on “Safest.” As you’ll see, JavaScript and a few other features will be automatically disabled on all sites. Be warned that this may cause some websites to not work properly. However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail. For more information, read more about the most secure email service providers in my other post. Now that you’ve completed the download, it’s time to install the Tor browser on your device.
Most of what you see in search results is just a small slice of the internet. In fact, only about 4% of the web is indexed, meaning it shows up in standard search engines. Simeon is a seasoned cybersecurity expert with a wealth of experience, certified in various IT domains. Known for sharing knowledge and mentoring, with a passion for ensuring privacy and data protection. A valuable contributor to open-source projects and a recognized professional in the field. A Virtual Private Network, or VPN, simply lets you access the dark web.

Report It To The Authorities (if It’s Safe To Do So)
However, on the dark web, JavaScript can also be exploited by hackers to track your activity or deliver malware to your device. To reduce the risk of these threats, it’s highly recommended to disable JavaScript when browsing dark web sites. If you want to access the dark web, your first step toward a more private experience should be to secure your internet connection and data with a reliable VPN.
Users also face the potential danger of government monitoring and surveillance — or scams and fraud, and other activities that can lead to financial loss and identity theft. Without a VPN, the first server in the Tor network (the entry node) can see your real IP address, and your internet service provider (ISP) can see that you’re accessing the dark web. This creates a privacy risk even if they can’t see what you’re doing on the dark web. Plus, in some regions, accessing the dark web alone may raise suspicion or get you flagged for extra monitoring. In the deep net, web crawlers are blocked from accessing web pages to gather information for indexing, so the content remains hidden. Some content and services on the deep web are indexed by search engines, but paywalls or password protection prevent access.



