
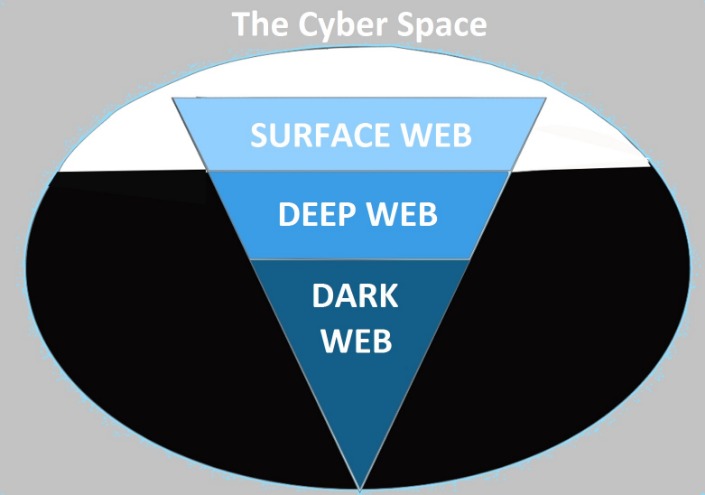
Radar Rundown Private search engines use the metasearch or proxy search model and the proprietary cr… The dark web is a part of the deep web that contains websites not included in the mainstream search engine index. The deep web is not a series of sites but a storehouse of records, including email accounts, medical records, private messages, and more.
PGP Encryption
It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. You should never use your personal information on the dark web anywhere else in your life.
Is It Illegal To Access The Dark Web?
Even if one Ares link is down, alternative onion mirrors keep the Ares darknet marketplace always available and accessible. What distinguishes Ares from other markets is its innovative approach to dispute resolution, multi-signature escrow system, and vendor verification process. These features combine to create a marketplace that’s both secure for buyers and fair for sellers. While technological innovation remains a force for progress, its use within the criminal underworld signals a need for more coordinated global responses. In 2025, the dark web no longer exists in isolation—it interacts with mainstream platforms, influences real-world crime, and exploits cutting-edge financial systems. The ability to understand and counteract its growth will define the future of cybersecurity and digital law enforcement.
DrugHub Darknet Market – an underground online marketplace, is structured around the dual roles of vendors and community members, blending elements from its pre… As we approach the year 2024, the dark web markets are expected to undergo significant changes. With new technologies and regulations emerging, it’s essential to stay informed about the latest trends and developments.
You can find legitimate products such as basketball shoes, apparel, research papers, and other items on the dark web. Of course, you can also find plenty of illegal items such as hacked Netflix accounts, stolen Social Security numbers, credit card account numbers, firearms, and drugs, too. I always cross-reference links from multiple verified sources before visiting any dark web address. A reliable VPN encrypts your traffic before it enters the Tor network, preventing surveillance from your ISP or malicious actors.
Security Evolution
- For listings with a holding and placeholder price, we searched for the same product from the same vendor to find a replacement price.
- The three nodes separate your IP address from your destination and enable two individuals to communicate without either party, or any middleman, knowing who the other is.
- Quality and validity of the data it provides justify its higher cost over other marketplaces.
- This means your activities cannot be traced or your browser history exposed.
- As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web.
It was the first big site where people could anonymously buy drugs using Bitcoin, and it gained a lot of attention, until it was shut down by the FBI in 2013. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. Darknet markets — also known as cryptomarkets — provide a largely anonymous platform for trading in a range of illicit goods and services. Accessing the dark web can only be done using specific browsers, such as TOR Browser. Advanced tracking tools help you monitor price trends, vendor reliability, and product availability across the Ares darknet marketplace. The Ares onion address provides access to a decentralized marketplace that prioritizes security without compromising functionality.
Use A VPN

Classic darknet markets sell diverse illegal goods; data stores focus on leaked or stolen data like credentials, databases, and ID records. Secure, anonymous transactions with the most trusted darknet marketplace since 2021. Featuring escrow protection, Monero support, and a user-friendly interface. The intersection of cryptocurrency and dark web markets continues to challenge traditional models of law enforcement and finance.
- However, this will likely lead to the rise of new, decentralized groups like RansomHub.
- These domain names are not registered with a central authority but are instead derived from cryptographic keys.
- Generally, complete anonymity and invisibility to the search engines are the two essential features that define the darknet.
- Many dark web search engines are available, and no single option is objectively the best.
- The dark web marketplace ecosystem has seen a significant transformation in 2023.
Pharmaceuticals And Digital Goods Thrive On Darknet Platforms

There’s also a privacy angle—some users live in countries with censorship or surveillance, and the dark web gives them a space to communicate or access information more freely. This is why it’s crucial to always check for updated Ares links from trusted sources before attempting to access the marketplace. Our secure messaging system prevents metadata leaks and ensures private conversations remain private. Ares doesn’t require email verification or personal details, protecting your identity at all times.
Where Funds Go After Leaving Darknet Markets
These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. You can’t access these .onion sites from your normal web browser like the one you’re probably viewing this page on. To make its journalism more accessible to readers around the world, the New York Times launched its onion service in 2017.
Some users also share links on encrypted apps like Telegram or Keybase that you can check. Unlike other search engines, it does not collect or share web activities and personal data of users. It’s a hidden collective of sites that you could only access through a special browser. Since all activity on the dark web is anonymous by default, it is definitely where the murkiest transactions on the internet take place.
The service emphasizes privacy with zero-knowledge encryption and no registration requirements. My tests showed reliable performance for smaller files, but larger transfers can be slow due to Tor’s limitations. TorBook aims to be a privacy-focused alternative to mainstream social networks. It emphasizes anonymity while providing familiar social media features.
How To Use Tor, And Is It Safe To Access The Dark Web?
Our advanced escrow system requires multiple signatures to release funds, preventing exit scams and ensuring fair transactions for both buyers and sellers. Browse listings, read vendor reviews, and make your first purchase with escrow protection. For a local machine configuration, he recommends a computer purchased for cash running Linux, using a local Tor transparent proxy.

Litecoin, Zcash, and Dash also see usage, though Monero and Bitcoin dominate the dark web. Some marketplaces have even mandated Monero-only transactions, underscoring a strong preference for privacy-focused coins over traceable ones. Cryptocurrencies have replaced fiat currencies as the default medium of exchange on the dark web. Bitcoin continues to lead as the most widely accepted digital currency due to its high liquidity and global acceptance. However, its transparent blockchain has prompted users to shift toward more private alternatives. Nexus represents the upcoming market generation that instills trust in its users.
Malicious Software
Once contact is made, vendors transition discussions to secure messaging apps to complete the transaction. STYX Market, for example, concentrates on financial crimes, offering access to hacked bank accounts, forged documents, and money laundering services. Other platforms concentrate solely on narcotics, counterfeit items, or stolen digital identities. This specialization allows vendors to cater to targeted buyers and refine their offerings. These platforms cater to specialized criminal sectors, making them more efficient and organized.
This adds extra protection since opening Tor itself encrypts your traffic. The Tor browser allows you to browse the internet anonymously and visit inaccessible sites. For this reason, you must watch out and avoid opening anything that looks suspicious to you.



