
With all of that in mind, you need to tread carefully when browsing, in terms of the sites you visit and the other users you interact with. Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place. Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too.
It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites. It offers top-of-the-line security and fast speeds for a smooth browsing experience on the dark web.
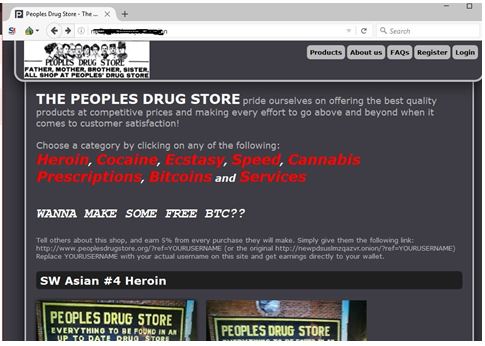
Navigating With Dark Web Search Engines
- Cybercriminals often disguise malware within legitimate-looking files to trick users into compromising their own security.
- While it does host illegal activities and shady content, it also supports legitimate uses like secure communication for activists, journalists, and whistleblowers in oppressive regimes.
- There are several whistleblower sites, including a dark web version of Wikileaks.
- As search engine crawlers do not catalog these pages, you would need to know the exact link to access a website in this area of the internet.
- There’s evidence that law enforcement agencies in freer countries operate many exit nodes for monitoring and surveillance purposes.
If you need to create accounts on dark web services, use a burner email and never reuse usernames or passwords from your real life. If you must purchase anything on the dark web — which I don’t recommend — you should always pay in cryptocurrencies. I2P is a private network built for secure, anonymous communication. Instead of the onion routing Tor uses, I2P relies on unidirectional tunnels and garlic routing, which bundles multiple messages together for better traffic obfuscation. It uses its own internal DNS to access “eepsites”, not .onion addresses.
Caution: Safety Comes First When Visiting Dark Web Links

For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography. Therefore, the legality of the dark web will mainly depend on how you use it. You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom. The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity.

More Ways To Stay Safe On The Dark Web
While tools like the Tor Browser offer strong anonymity, things like downloading files, enabling JavaScript, or logging into personal accounts can expose your identity. Using a VPN and following safe practices greatly reduces the risk of being tracked. Unlike the clear web, where websites are often rated or reviewed, most dark web sites are unregulated.
Dark Web VPN: FAQs

In due course, the framework was remodeled and made public as a secure browser. While it might appear tempting to venture into the dark web, it’s crucial to understand that the risks here are far more severe compared to the deep web. Therefore, if you do decide to explore it, exercise extreme caution. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. Some markets are relatively short-lived (thanks to law enforcement), but others are notorious enough that they survive, for instance, Silk Road, AlphaBay, and Hansa. These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything.
How To Access The Dark Web Using The Tor Browser
Using a legal browser will not make your actions fall to the right side of the law. Understanding that the nature of the internet meant a lack of privacy, an early version of Tor was created to hide spy communications. Eventually, the framework was repurposed and has since been made public in the form of the browser we know today.
Who Is Tracking Your Internet Activity, And Why?
The best VPN options are paid-for and subscription-based, as many free options will either throttle your speed or collect your data. However, today’s most popular search engines — including Google, Bing, and DuckDuckGo — only index a portion of the internet. For most people, Tor over VPN is the safer and more practical choice. It protects your real IP address even if Tor leaks, is easier to set up, and works with most major VPN services.
As a general rule, never download anything at all from the dark web. There are all sorts of threats on the dark web, and it’s all but impossible to verify whether a file is legitimate, so you’re likely to inadvertently download malware to your device. Firstly, it could jeopardize your anonymity if you submit any kind of personal information during a dark web browsing session. Secondly, there are many malicious, fake, and phishing sites on the dark web, which might look like sites you trust but are actually designed to steal your data. There are many good and legitimate reasons to step into the dark web, but you should always do so with caution. For instance, did you know you can unknowingly break the law while browsing the internet?
One of the darkest aspects of the dark web involves human trafficking, illegal pornography, and other forms of exploitation. Hacked data, credit card details, and personal information are frequently traded on the dark web. Illegal marketplaces like the now-defunct Silk Road have facilitated drug sales, arms trading, and other prohibited activities.
Secure Your System And Mental Well-being
Each relay on the Tor network only knows the previous and next relay in the chain, ensuring that no single entity can trace the complete path of data transmission. Additionally, much of the materials on the dark web are illegal, and unknowingly downloading such content can implicate you in criminal activities punishable by laws. If your device is infected with malware, read our guide to remove malware from your computer. Security solutions like anti-virus software protect your system and network from malware and other threats. The dark web, being a hub for criminal activities like identity theft and malware distribution, exposes you to various security threats like malware or phishing. Many people use it for privacy-focused communication, whistleblowing, or accessing restricted information in censorship-heavy regions.
While it provides anonymity, privacy, and access to censored information, it is important to approach the Dark Web with caution and adhere to ethical guidelines. Remember, even with these recommended websites, exercise caution and verify their reputability before engaging with them. The Dark Web carries risks, and it’s important to stay informed and vigilant while navigating this hidden part of the internet.
Are All Websites On The Dark Web Illegal?
From real-time alerts vetted by Cyble’s Security Operations Center (SOC) to AI-driven risk tagging, Cyble enables faster, more informed response decisions. Its deep insights into cybercrime forums, compromised card databases, and exposed assets give security teams a critical edge. Look for features like real-time alerting, coverage of multiple dark web forums and marketplaces, credential and data leak detection, and integration with your existing security stack. Strong vendor support, customizable alerts, and compliance alignment are also key to ensuring the tool delivers actionable insights, rather than just noise.
Estimates place the size of the deep web at between 96% and 99% of the internet. Only a tiny portion of the internet is accessible through a standard web browser—generally known as the “clear web”. Many cybercriminals operating on the dark web have been arrested by law enforcement agencies, proving that anonymity isn’t foolproof.



