Your ISP still knows you’re using Tor, and entry nodes can see your real IP address. A VPN adds protection before Tor, closing these gaps without breaking access to .onion sites. Whonix uses Oracle Virtualbox to run two virtual machines (VMs) on top of your currently installed OS (Windows, Linux, or Intel-based macOS). The Whonix Gateway VM handles Tor processes, and the Whonix Workstation VM runs user applications on an isolated network. This prevents data from leaking between applications and makes your Internet traffic more secure. Your download and upload speeds may be slower, but that is the tradeoff for secure Internet browsing.

Safety Precautions
Darknet allows you to access the dark web and its hidden resources securely. It enables navigation through Onion websites and ensures an anonymous browsing experience by shielding online activity from third-party surveillance. Whether you are exploring academic content, legal data, or unique marketplaces within the dark web, the app’s structure ensures user safety and discretion. These websites use the Tor network to provide anonymity and privacy to their users.
How To Change The Onion Browser’s Security Settings On IPhone

Journalists in overly restrictive countries also appreciate the anonymity of the dark web. The users of the dark web are typically aiming to block governments from snooping on them. This can often be for political reasons, but also because they may be involved in illegal activities, such as the ones listed above.
Verify onion URLs

If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node. Though no one should bat an eye just because you’re attempting to access the dark web, keep in mind that in some countries, like the United States, even a simple foray can get you in trouble. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web. For recommendations on choosing a VPN, look for expert reviews and articles.
Added Security: Use A VPN
Despite the dark web sometimes catering to criminals, some of the marketplace items are entirely legal. For example, art and jewelry can be found on the dark web (and not necessarily after being stolen). Hackers don’t always attack companies and individuals to use the breached data themselves. They can sell that stolen information on the dark web to other scammers and criminals. However, many activities that take place on the darknet are illegal, and you should be aware of this before accessing it.
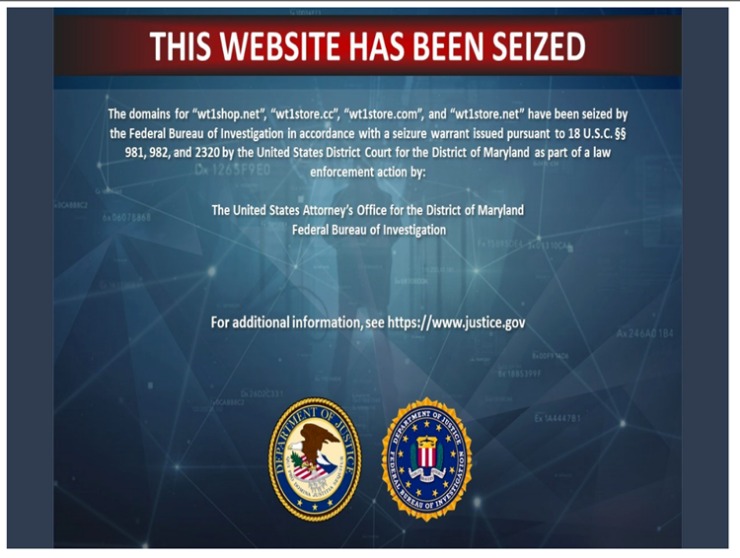
Sharing or even possessing abusive or exploitative content is also a very serious offense. Police do investigate and prosecute crimes that happen on the dark web. For example, in June 2025, Europol and U.S. partners shut down Archetyp Market, one of the longest-running drug markets on Tor (Europol 2025)4. This process, called “onion routing,” makes it very hard for anyone to trace where you’re connecting from. With Tor, you can access regular websites as well as special Dark Web addresses that end in “.onion”, which you can’t open in standard browsers like Chrome or Safari.
Step-by-Step Guide: Access The Dark Web On Any Device
If you plan to purchase on a dark net marketplace or dark web commerce sites, you’ll need to create a fake identity. Remember only to make purchases using digital currencies and never provide any online banking login details. The Tor Onion Browser is essential for accessing the dark web, designed for user anonymity. Unlike the regular internet, the dark web doesn’t use standard URLs or search engines. Instead, sites have complex .onion addresses, making them difficult to find without the exact URL. Yes, you can access the darknet on your mobile device using the Tor browser.
Best Dark Web News Sites Offering Factual Information
Let’s now explore the step-by-step process of preparing your Android device to access the Dark Web. Therefore, before embarking on your journey to explore the Dark Web, it is crucial to familiarize yourself with the legal implications and the risks involved. Always remember to abide by the laws of your country and exercise caution while browsing the Dark Web. Law enforcement agencies around the world are constantly monitoring the Dark Web to identify and apprehend individuals involved in illegal activities. They employ advanced techniques and undercover operations to bring perpetrators to justice. Depending on the device you’re using, there are 2 browsers you need to access the dark web on your phone.

The Tor network is a volunteer-run network that allows users to browse the internet anonymously by routing their traffic through a series of servers around the world. The Dark Web refers to a part of the internet that is not indexed by traditional search engines and requires specialized software, such as Tor, to access. It is a network of websites and online communities that exist outside of the mainstream internet, offering users a higher level of anonymity. There are several reasons why someone might want to access the darknet on their Android device. For one, it can provide a greater level of privacy and anonymity than traditional internet browsing. Additionally, the darknet can be used to access content that is censored or blocked in certain regions.
Install free Avast Secure Browser to get automatic incognito browsing, block web tracking, and protect your personal data. The default Tor search engine is a dark version of DuckDuckGo, but there are other dark web search engines you can use on Tor. If you’re interested in anonymous browsing, first check whether Tor, or even VPNs, are legal in your country. Using a proxy server in combination with Tor Browser can help to hide the fact that you’ve connected to the dark web, but it won’t confer any additional cybersecurity benefits. Finally, you need to enter website addresses to access content on the dark web since you can’t browse by entering a search query as you can on the clear web. It’s highly probable this software program is malicious or contains unwanted bundled software.
- While Tor provides a high degree of anonymity by routing your internet traffic through multiple servers, thereby masking your IP address, it isn’t infallible.
- Hackers there might have tricks up their sleeves to track your location through GPS or WiFi, and they could potentially access other sensitive information on your device.
- This is one of the most valuable resources available on the dark web.
- Users need to exercise caution when navigating this hidden realm of the internet.
- The best way to prevent your browsing activity from alerting authorities is to avoid sites with illegal activity altogether — another reason to only visit sites you’ve researched and trust.
- Although that’s partially true, there are plenty of good reasons to access the dark web, and a major benefit is anonymity.
- With your device running a Tor browser, you can go to Tor-specific sites – those with an .onion suffix — or also visit the usual sites on the open web.
- While it is not flawless in protecting user privacy, it works well enough to give users much more privacy in where they go, the content accessed, and protecting their identity and location.
- Your download and upload speeds may be slower, but that is the tradeoff for secure Internet browsing.
- This process is automatic, and it may take a few minutes to establish a connection.
- Alternatively, if the website has turned the onion URL into a link, you can click on that in the Tor browser, and it will automatically open the dark website.
In most cases, every search engine will give you even millions of results. This shows that there are a lot of web pages existing online in the Clearnet. According to some statistics, the number reaches about 1 billion pages available worldwide. Tor for Android is developed by the Tor Project itself, while the Onion Browser is the recommended option for iOS users. These browsers offer the best security and privacy for browsing the dark web on mobile devices.
While the Dark Web offers anonymity, it is important to remember that illegal activities thrive in this realm. Exercise caution at all times and use your best judgment when browsing and interacting on the Dark Web. It’s important to note that the Tor Browser is based on the Firefox browser and provides a secure and privacy-focused browsing experience. It automatically blocks trackers, defends against surveillance, and allows you to access websites on the Dark Web anonymously.



