
Deep web pages can’t be accessed through a simple search, as search engines do not index them — it’s a layer of the internet only accessible to people with a specific link or login credentials. The open web, also called the surface web, includes any public web content that is indexed by search engines. Webpages on the open web will show up in search results on sites like Google and Bing. Though a large volume of traffic visits on the open web every day, it only represents 4% of the content on the internet. If you carefully follow the six tips we have provided, you will be well on your way to accessing the dark web safely, securely, and anonymously.
The final step before you can start browsing with relative peace of mind is to conduct an IP leak check. The difference between the surface web and the deep web is that pages, websites, and content on the deep web are only accessible to authorized users with the appropriate credentials. In other words, these are pages that aren’t indexed and therefore can’t be found by a typical search engine.
Do I Need A VPN To Access The Dark Web?
These are platforms where leaked or stolen data, including personal information, passwords, and credit card details, are bought and sold. They often provide access to vast amounts of compromised data from previous hacks or breaches. The deep web includes non-indexed databases and private portals, while the dark web specifically requires Tor and includes .onion sites. Avoid sharing personal information, downloading unknown files, and engaging in illegal services. While not mandatory, using a VPN adds an extra layer of privacy and security by hiding Tor usage from your internet service provider. Accessing the dark web is legal in India as long as you do not engage in illegal activities such as buying drugs or hacking services.
Cryptocurrencies And Financial Anonymity
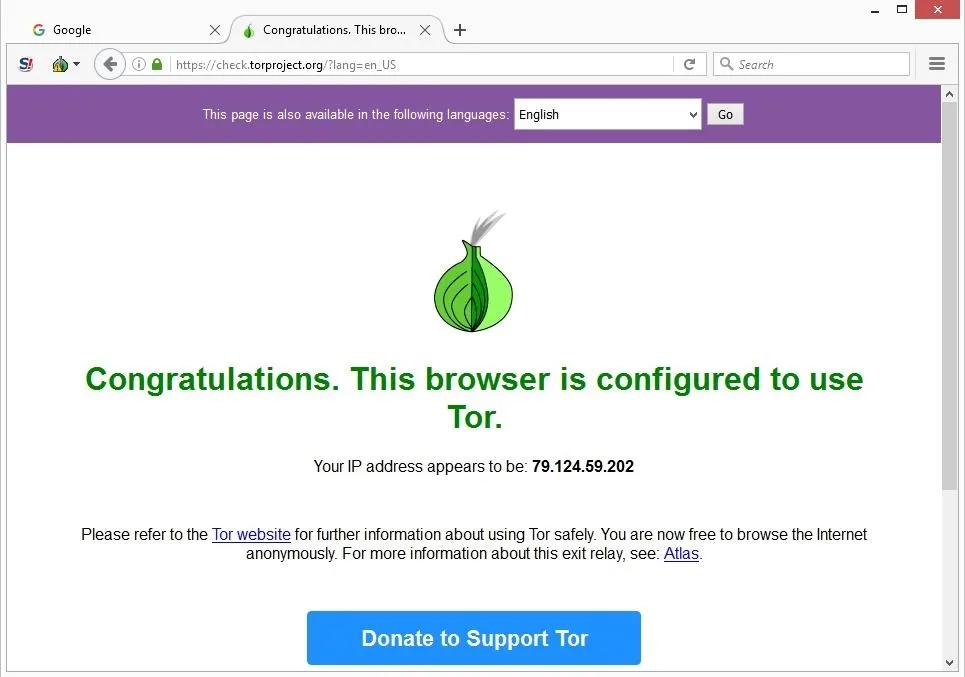
You won’t be able to search the dark web with a regular browser (such as Chrome or Firefox). Besides, your online activity on such browsers is visible to your ISP unless you connect to a VPN service. Yes, you definitely need a VPN if you want to access the dark web on your phone.
- This hides your Tor usage from local networks, masks direct Tor connections, protects against network-level surveillance, and reduces the risk of being flagged for accessing privacy tools.
- A logless VPN, which doesn’t store any traffic logs nor session logs is highly preferable.
- If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough.
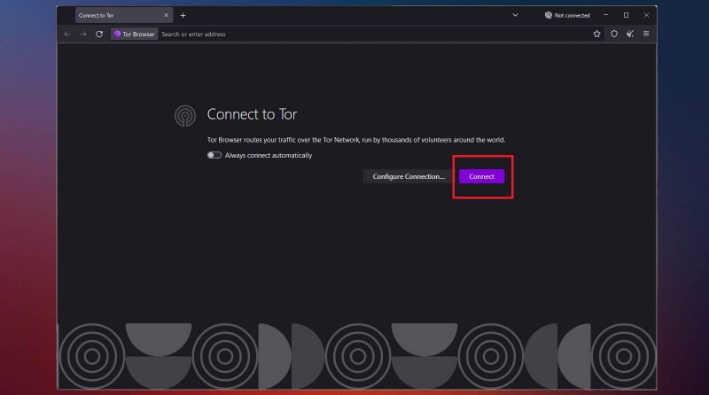
- After clicking the “Connect” button, you are now connected to the Tor network.
- If you need to create accounts on dark web services, use a burner email and never reuse usernames or passwords from your real life.
- As a result, it would be difficult to locate you or trace the dark web activity back to you.
Examples Of Popular Dark Web Resources
That way, even if something goes wrong, your main machine stays untouched. There are lots of perfectly legitimate reasons you might want to access all that shady content. The dark web is full of unknown and potentially dangerous content. Clicking on links there might take you to illegal or harmful material without warning.
Some of these sites can be found through regular web browsers, but you’ll then need to switch over to Tor once you’ve got the onion links you want to follow. The invisible web is made up of data and information that is not indexed and cannot be searched for by using traditional search engines. It includes media and archives which cannot be crawled and indexed with current search engine technology.
Myth 1: The Dark Web Is Only Used For Illegal Activities
The easiest way to access Tor is through a special browser known as the Tor Browser. You might want to hide your Tor Browser download using a VPN and your existing browser’s private/incognito mode. Dark web commerce sites have the same features as any e-retail operation, including ratings/reviews, shopping carts and forums, but there are important differences.
How To Get On The Dark Web In 2025: A Step-by-Step Guide
These search engines can help you discover .onion sites related to your interests. However, note that dark web search engines don’t index as many sites as regular search engines, so results can sometimes be limited or outdated. Tor isn’t available for iOS due to Apple’s restrictions, but you can still access the dark web on your iPhone using the Onion Browser, which is from the Tor Project. This app connects to the Tor network, allowing you to visit .onion sites. But with the NSA setting up fake exit nodes, and growing concerns about the overall security of the network, you may need a VPN as well, if you want to ensure your privacy. Lastly, navigating the Dark Web also carries legal risks, as unintentional engagement with illegal platforms or content can lead to severe consequences.
- These efforts could very well include accessing the dark web to help victims and hunt down criminals.
- For recommendations on choosing a VPN, look for expert reviews and articles.
- In brief, while exploring the dark net isn’t inherently illegal, you should be careful about the material you interact with.
- Unlike traditional browsers, this will route your internet traffic through an anonymizing network and mask your IP address.
- Locating surface web websites is possible because search engines can index the web via visible links (a process called “crawling” due to the search engine traveling the web like a spider).
Step 4: Boot Into Tails OS From The USB Drive

The Dark Web—a hidden part of the internet accessible only through specialized tools like Tor—often conjures images of mystery, intrigue, and even danger. However, navigating this hidden digital landscape in 2025 presents heightened security risks, from advanced cyber threats to targeted surveillance. This guide provides clear, step-by-step instructions to safely explore the Dark Web using Tor, helping you stay protected, informed, and anonymous. No, simply accessing the dark web isn’t illegal in most countries. The dark web is just a part of the internet that isn’t indexed by traditional search engines and requires special software like the Tor Browser to access. For example, journalists, whistleblowers, and privacy-conscious individuals often use it to communicate securely or access uncensored information in restrictive regions.

Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia. The subreddit r/deepweb is a good starting point for asking more experienced users about how to search the dark web and deep web for the content you want. Lastly, The Hidden Wiki is a collection of dark web links — but the links may not work and can lead to dangerous websites.
How To Access The Dark Web On An IPhone
A VPN keeps all of your online activities – including your web browsing, online gaming, streaming, and file-sharing – undercover and safe from being tracked or recorded. Another reason you don’t want to use the Tor Browser for your daily web browsing is that it draws attention to you. The Tor Browser prevents your ISP from seeing what websites you’re visiting, but it does not prevent the ISP from seeing that you’re using Tor. To be on the safe side, we recommend combining the Tor or onion browser with a secure VPN, such as NordVPN.
Guide To Accessing Tor Via Tails OS On A USB Thumb Drive:
Besides offering a secure connection, Forest VPN is designed to use less battery, reducing your carbon footprint. Its competitive pricing ensures that robust privacy protection is as affordable as a cup of coffee. Plus, with no logs or data collection, your activities remain your own secret. The dark web often conjures images of clandestine meetings and shadowy transactions. However, it is also a vital resource for privacy-seekers and those needing unrestricted access to information.
Why Do The Darknet And Deep Web Exist? Legitimate Uses
It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims. Hacker services against banks and other financial institutions are offered there. There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes. The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures. Those who access the dark web do so via the Tor (The Onion Router) browser. But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web.



