
The dark internet is designed to provide anonymity by keeping communication private through encryption and routing online content through multiple web servers. While the dark web is often depicted as an anarchic forum for criminal activity, that’s not necessarily true. The darknet is simply an anonymous space on the web that can be abused or appreciated in turn. The open web, also called the surface web, includes any public web content that is indexed by search engines.
Core Anonymous Networks And Protocols
- For example, cyberattacks and trafficking are activities that the participants know will be incriminating.
- The Tor Browser is automatically configured to provide a certain level of privacy and security.
- The use of the dark web raises suspicion as it shows there is something you want to do privately.
- Other privacy networks like I2P, Lokinet, and Freenet offer different layers of security and anonymity.
If you must download a file, verify its source and consider using a sandbox or virtual machine to open it safely, away from your primary operating system. A VPN also helps protect you from risks in the Tor network itself. The VPN encrypts your traffic before it enters the Tor network and all the way to its destination, so your traffic remains protected. Its goal was to allow ships to communicate with each other and their bases without revealing their location.
Be Cautious Of Links
It does this by bouncing users’ and sites’ traffic through multiple relays to disguise where they are. Most corporate and public sites work hard to make sure that these web crawlers can easily find them. This makes perfect sense as the entire purpose of creating a website is so that people can access your content and/or buy your products. Most sites do this by deliberately placing “meta tags” in their website code to make it easier for crawlers to catalog them properly.
Best Dark Web Sites 2025 – Detailed List
The dark web is a playground for hackers, cybercriminals, and people with nefarious objectives. We strongly advise you against visiting it, even if your intentions are good. Dark web websites don’t bear Internet Corporation for Assigned Names and Numbers (ICANN) domains, such as .com. They use a scramble naming structure that combines a string of letters and numbers to create URLs that are impossible to remember. In addition to the below categories, I also exclusively cover adblockers, authenticator apps, hardware security keys, and private messaging apps.
This infects a user’s device and essentially blocks them out of it until they pay a “ransom,” usually in the form of cryptocurrency (so it’s harder to track and recover). Users could accidentally fall victim to ransomware just by clicking the wrong link or downloading a file on the dark web. If you’re in the U.S., you can make use of helpful tools like ExpressVPN’s Identity Defender to inform you if and when any of your data ends up on the dark web.
Illegal Streaming Sites
The Tor Browser also features many built-in protections that protect against tracking and fingerprinting. Navigating the Dark Web can be a complex endeavor, but you don’t have to do it alone. Reputable organizations, security researchers, and privacy advocates provide a wealth of insights, tutorials, and software to help you explore safely and responsibly. Below are some trustworthy starting points and authoritative references. By familiarizing yourself with these networks and protocols, you gain a clearer understanding of the diverse strategies people use to stay hidden online. Each network has its strengths, drawbacks, and intended use cases.
How Do I Verify An Onion Link Is Safe?
And with many unfamiliar-looking sites on the dark web, it’s harder to distinguish safe websites from shady ones, and easier to fall victim. You can access the dark web on mobile with a dedicated dark web browser app. Install a mobile dark web browsing app — like Tor browser for Android or the Onion browser for iPhone — and enter an onion URL to start browsing. Similar to using a standard web browser to access the open web, the act of using Tor or a dark web browser to access the dark web is not illegal in and of itself. It is illegal to perform illegal acts on the dark web, regardless of the level of anonymity provided by the platform.
Do Not Share Personal Information
Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer. It includes all the essential productivity software, including MS Word and an email client. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy.
In this tutorial, we’ll explain how to access the dark web in complete privacy and cover a few more important factors to consider before starting. Given the amount of illegal and unsettling content on the dark web, there is always a risk that you might encounter something that could disturb you. Even if you’re only attempting to visit legitimate sites, one wrong click could expose you to content you would rather not see.

Hacking And Cybercrime Services
By utilizing a VPN and the Tor Browser, you can ensure a higher level of anonymity and security when accessing the Dark Web. Remember to choose a reliable VPN service, follow the recommended security practices, and exercise caution while exploring this hidden part of the internet. When accessing the Dark Web, it’s crucial to protect your personal information. Avoid using your real name, email address, or any personally identifiable information.
There’s a fascinating thread on Reddit (not remotely safe for work) where dark web users share their stories. Some of the tales are enough to make you tape over your webcam and disable your router just in case. Think of it as the dodgy bit of town where sensible people don’t go after dark. Since your connection is routed through multiple tor relays, page loading times can be very slow making effective searching extremely time-consuming.
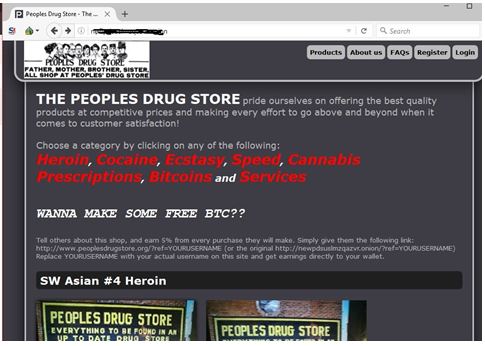
Within the deep web is another part of the internet called the dark web. Dark web sites are so well-hidden they can’t be accessed with normal browsers such as Chrome, Firefox or Safari. The dark web can only be accessed using a special browser called Tor. Illegal drug marketplaces like the Silk Road have been hijacked for police surveillance in the past. By utilizing custom software to infiltrate and analyze activity, this has allowed law officials to discover user identities of patrons and bystanders alike. Even if you never make a purchase, you could be watched and incriminate yourself for other activities later in life.
Even without monitoring your browsing activities, DuckDuckGo will offer decent answers to your questions. This article lists some of the best dark web websites you can visit securely. Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun. Ensure that you’re aware of what is permissible in your jurisdiction. I2P (Invisible Internet Project) is an open-source network designed to allow anonymous and private communication.



