
Unlike VPNs, which also provide anonymity, it reroutes the users’ traffic through a network of nodes rather than just a single server. This way, Tor makes it much more difficult to trace the traffic back to the original user. Additionally, Tor enables users to access darknet sites hosted on .onion domains, something most common browsers can’t do. Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products.
Between January 2019 and September 2023, the majority of those queries came from underdeveloped countries with well-documented instances of internet censorship. Pakistan topped the list with 100 index points (maximum), followed by Kenya (89 points) and Myanmar (87 points). The top 10 also included Bangladesh (78), Ethiopia (75), Nepal (75), Cameroon (67), Tanzania (66), Nigeria (65), and Sri Lanka (63 index points). The aforementioned Tor browser has established itself as the go-to browser for accessing the Dark Web. Though there are other browsers with similar functionality, Deep Web statistics point to Tor as the most popular — with 5.92 million new downloads worldwide in 2023’s third quarter. Chainalysis also noted that some markets are openly advertising their wares in Russia, with giant 3D billboards (Kraken Market) and QR codes on subway trains (Mega Darknet Market).
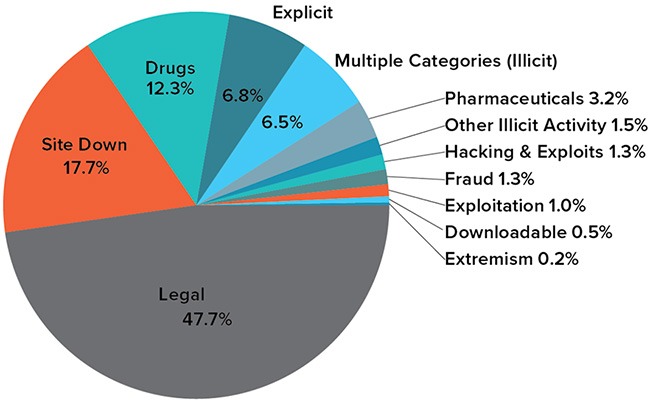
Recognizing the role of darknet markets in trafficking stolen data, we conducted the largest systematic examination of stolen data markets that we are aware of to better understand the size and scope of this illicit online ecosystem. To do this, we first identified 30 darknet markets advertising stolen data products. Nonetheless, threat actors adapted, with many choosing to move to the “RuTor” forum for communications and to decentralized platforms such as Telegram-based shops for drug advertisements, as well as offline sales. Russian-speaking DNM customers were historically frequent users of RuTor, where they would exchange information.
Darknet Market Trends In 2025
They follow a proactive approach that typically looks like disrupting the cybercrime business model by targeting the specific online ecosystem. Below the deep web is the darknet (or dark web), which is even harder to access due to its unsearchable, encrypted and private nature which affords users complete anonymity. This part of the web isn’t accessible by traditional search engines, and so isn’t picked up by web crawlers. To access pages and information within the deep web, users require the correct authorisation and credentials.
How Much Is Stolen Data Worth?
At that price, Maltese passports were the most expensive forged physical documents on darknet markets. French, Dutch, and select EU passports all cost $3,000 apiece, Polish passports went for $2,500 each, US passports sold for $2,000, while Lithuanian passports cost $1,800 each. Other popular physical documents included EU driver’s licenses ($2,000 apiece), EU national IDs ($1,700 on average), forged US green cards ($450), and IDs of several US states ($200). BlackSprut placed first in a recent ranking of Dark Web marketplaces based on the amount of money deposited between January and November 2022. Known for drug trafficking and its alleged links to Russia, BlackSprut was the subject of a media controversy when several billboards for the marketplace were spotted in Moscow in early 2023. According to news reports at the time, it was unclear if these were paid ads or if the electronic billboards were hacked.

Only 67% Of Tor’s Daily Users Engage In Illegal Activity On The Dark Web
The tool is still available today, and interested parties simply need to enter their email address to place an inquiry. If the address is in one of the cybercrime datasets, the person will receive an email that includes personalized instructions on how to clean up their computer and make it safe again. In the first 24 hours of launching Check your hack, two million people took advantage of the service. So far, five million people have used the tool, and over 13,000 victims have been notified that their computer was infected, and received instructions to help them make their device safe again.
The Significance Of This Data
On a smaller scale, Mega Darknet Market placed a few ads with QR codes in public places like Moscow subway trains. While tactics like these may have helped boost revenue for both markets, again, they have yet to match Hydra’s sizable financial success. According to Check Point Research, schools and other educational institutions were the most targeted sectors, with attacks rising by 43% compared to 2021. The same report showed that cyberattacks on the healthcare industry grew by 86% in 2022 compared to the previous year. We review and list tools and products without bias, regardless of potential commissions. Further market diversification occurred in 2015, as did further developments around escrow and decentralization.
Surge In New Scams As Pig Butchering Dominates
They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails. If you ever decide to explore the dark web, protecting your identity is crucial. Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. He was also ordered to pay restitution of $183 million — the estimated value of Silk Road’s drug and counterfeit ID sales. Another way to gauge people’s interest in the Dark Web is to examine the percentage of those who look up the term “Dark Web” on Google.
Silk Road (2011–
The darknet has become a hub for secure and efficient online trade, offering users a platform to engage in transactions with a high degree of anonymity. Among the most notable markets, AlphaBay and Hansa have established themselves as leaders due to their robust security features and user-friendly interfaces. These platforms utilize advanced encryption protocols and escrow systems to ensure that both buyers and sellers can conduct transactions with confidence. We believe that advances in artificial intelligence can provide law enforcement agencies, financial institutions, and others with information needed to prevent stolen data from being used to commit fraud.
The Saga Continues: More Dirt On The Salesforce–Drift Breach
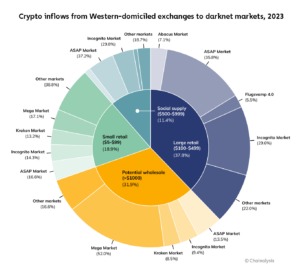
Another topic in modern DWMs is the transactions made with cryptocurrency and the concept of crypto laundry. According to TRM Labs, Incognito launched in October 2020 and remained active until March 2024. In that time, it facilitated more than USD 100 million in drug sales, including hundreds of kilograms of cocaine and methamphetamine, alongside heroin, LSD, MDMA, oxycodone, ketamine, and misbranded prescription drugs. Our research details a thriving underground economy and illicit supply chain enabled by darknet markets. As long as data is routinely stolen, there are likely to be marketplaces for the stolen information. Launched in 2015, the Russian marketplace, Hydra Market, was known for its trade in drugs among other things.

This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material. Thanks to worldwide media coverage of our findings, it has helped bring the conversation around personal information security further into the mainstream.
What Is The Largest Darknet Market?
In particular, we have seen the emergence of large-scale on-chain services that provide infrastructure for numerous types of illicit actors to help them launder their ill-gotten crypto. The falloff appears more serious for darknet marketplaces that specialize in stolen data used for fraudulent activity. The firm writes that the market for compromised credit card information and other forms of personal identifiable information never recovered from the shutdown of prominent fraud shops such as Bypass Shop.
- What’s even more alarming is that in April 2023, daily dark web visitors rose by 200,000 to reach 2.7 million.
- Identity theft, business email compromise (BEC), and account takeovers (ATO) are now fueled by vast troves of leaked data that are traded or given away for free across dark web forums, Telegram channels, and illicit marketplaces.
- Due to the concerted law enforcement action (and successive sanctions) against Hydra, cryptocurrency cash-out services are often wary of running under the same name as they did on the now-defunct market.
- The months and years after Silk Road’s closure were marked by a greatly increased number of shorter-lived markets as well as semi-regular law enforcement takedowns, hacks, scams and voluntary closures.
- Empire Market uses a multi-signature wallet system to ensure the security of its users’ funds, and it accepts Bitcoin and Monero as payment methods.
Mega Darknet Market is the dominant drug supply source for drug vendors on other darknet sites, holding a 63.4% share of that market. When looking at darknet drug markets serving Russia-based customers, Kraken Market captured 30.9% of market share, with Blacksprut and Mega Darknet markets closely following. As for drug markets serving Western customers, ASAP Market held a 25.0% share, followed by Mega and Incognito. Administrators and sellers on dark web marketplaces had a better 2023 than the previous year, pulling in an estimated $1.7bn in cryptocurrency-based revenues, according to new Chainalysis data. The combination of cryptocurrency integration, advanced security measures, and user-centric features has solidified the position of these markets as leaders in the darknet ecosystem.
Companies like CrowdStrike, IBM X-Force, DarkOwl, and Recorded Future have indexed hundreds of millions of pages to help businesses detect potential threats. The dark web isn’t going away, so you need to understand the risks and take necessary precautions to stay safe online. While the deep and dark web serve legitimate purposes, they also facilitate illegal activities and create difficulties for law enforcement. For a local machine configuration, he recommends a computer purchased for cash running Linux, using a local Tor transparent proxy. For operations security he suggests avoiding storing conversation logs, varying writing styles, avoiding mobile phone-based tracking and leaking false personal details to further obfuscate one’s identity.



