
Still, for those willing to put up with the inconvenience, the dark web provides a memorable glimpse at the seamy underbelly of the human experience – without the risk of skulking around in a dark alley. IBM Security X-Force, for example, reported that 29% of its ransomware engagements in 2020 involved REvil. The criminal groups that developed the malware gets a cut of the affiliates’ earnings, typically between 20% and 30%.
How To Watch The Google IO 2025 Keynote
- “Threat actors are wanting to drive focus on their own brand names to gain more notoriety for themselves, such as the regular launching of new ransomware group brand names and leak sites,” says Carroll.
- It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products.
- This diversity not only attracts a larger user base but also fosters competition among vendors, driving innovation and quality improvement.
- It works by sending internet traffic through volunteer-operated nodes all over the world.
- Specialized search engines, directories, and wikis can help users locate the data they’re looking for.
- Tor over VPN requires you to place some trust in your VPN provider but not your ISP, and is best if you want to access .onion websites.
This is an excellent way for Dark Web users to provide additional privacy protection when accessing the Dark Web. This trove of stolen data included names, addresses, Social Security numbers, and phone numbers, leaving millions of individuals vulnerable to identity theft. Shortly after the breach, a hacker group known as USDoD listed this data on dark web marketplaces, pricing it at a staggering $3.5 million. Kingdom Market is a newer darknet market that has been around since April 2021 but was only recently vetted for listing on Dread, the pre-eminent forum for markets on the dark web.
Is Tor Browser Free?
Instead of “.com” or “.org”, dark web addresses can be distinguished by the top-level domain, “.onion“. Based on Firefox, the Tor Browser lets you surf the clear and dark web. Ensure you download the Tor Browser from the official website to avoid downloading malware, spyware, or other viruses to your device.
(NOT) Lost In Translation – Why Your Language Doesn’t Matter To Cybercriminals
If you do need to access a dark web website for legitimate reasons, you can check directories like The Hidden Wiki to help find options. Later, Tor’s underlying code was released under a free license, and a nonprofit called the Tor Project was formed. In 2008, the Tor Browser was released, which made it easy for anyone to get on the darknet. The existence of an anonymous and hidden internet then allowed for alternative information channels and illegal websites to flourish. In 2002, the dark web grew significantly when researchers supported by the US Naval Research Laboratory built and released the Tor network.
Communication Security And PGP Encryption

As for the trade, OBMs host many marketplaces, whose functions include product listings, ratings, wallets and escrow services. The security of transactions is guaranteed by public key infrastructures and decentralized systems such as cryptocurrencies (Me, Spagnoletti, & Pesticcio, 2017). Moreover, such marketplaces have replaced many online forums supporting anonymous interactions between buyers and sellers of illegal goods. The aim of these studies is to explore the ways in which marketplaces operate (Van Hout & Bingham, 2014). Criminal case studies, netnographic observations and, in some cases interviews with buyers and vendors, have been conducted to explain how marketplace functions enable users to interact online.
Unique Features
The easiest way to access Tor is through a special browser known as the Tor Browser. You might want to hide your Tor Browser download using a VPN and your existing browser’s private/incognito mode. Upgrade your lifestyleDigital Trends helps readers keep tabs on the fast-paced world of tech with all the latest news, fun product reviews, insightful editorials, and one-of-a-kind sneak peeks. While visiting any of the sites you find on those Wiki sites, do not maximize your browser, as it can help identify you by your monitor resolution. Many people overlook the importance of regularly changing the WiFi network password. In addition, it has an automatic kill switch (Network Lock) that stops traffic if the VPN connection fails.

Dark Web Threats
Tor2door Market is among the largest dark net shops you must visit in 2025 if you’ve decided to visit such sites. On average, the marketplace consists of more than 11,000 items and 1000 vendors. In April 2016, its APIs were compromised, resulting in stolen messages. But since its relaunch, the developers are focusing more on operational security and ensuring that users can have a good experience on this site. It doesn’t use JavaScript, meaning the website won’t track your activities or exploit vulnerabilities.
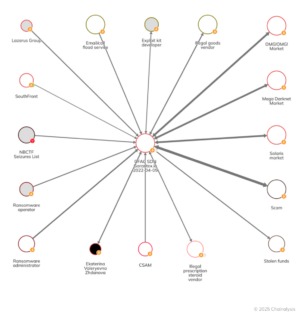
It has some advertisements on its home page, but they’re for popular searches and services to help get you started. These takedowns actively disrupt the immediate activities of these marketplaces and also cause a greater ripple effect, creating mistrust among other dark web users and making it harder for new markets to gain traction. As law enforcement continues to innovate and adapt, their ongoing efforts and international collaboration remain crucial in the fight against dark web crime. The strategies used by law enforcement to dismantle these marketplaces involve a mix of advanced technologies and old-fashioned detective work.

The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. Some users also share links on encrypted apps like Telegram or Keybase that you can check. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment.
Only use .onion links that come from legitimate sources like The Hidden Wiki. There’s even an option to set a timer on your most sensitive messages so they disappear after a set time period. The Hidden Wiki is the best way to start browsing the dark web because it contains dozens of links to popular .onion sites. The closures are unlikely to spell the end of darknet markets as new ones will no doubt emerge. Hundreds of millions of payment card details have been stolen from online retailers, banks and payment companies before being sold on online marketplaces such as UniCC. Ransomware leak sites are publicity sites where ransomware groups share the details of their latest victims.

The dark web limits online tracking, and there are many legitimate reasons people like journalists and activists use the dark web to remain private. But there are also many illegal activities that happen on the dark web. And just like in real life, using the dark web for criminal purposes is never legal. As always, protect yourself from online threats with mobile Android security or iOS security software. And use a VPN for Android or a VPN for iOSto get a secure, private connection. Tor is a web browser that lets you stay anonymous online or access the dark web.
Microsoft Word is one of the best word processors around, allowing you to craft powerful documents with an intuitive interface. If you know how to use Microsoft Word, you’re typically working with large files that span multiple pages. So, you’ll be happy to know there are several easy ways to delete a page in Word, including both blank pages and those you simply no longer need. To use the dark web safely, use as many privacy-enhancing tools or programs as you can, and do not identify yourself in any way to anyone for any reason.



