
A dark web search engine can help you surf sites on the Tor browser. Many who access the dark web do so by first connecting to it with the Tor (an acronym for the “The Onion Router”) browser. Navy and made public in 2004, Tor is the most popular dark web browser because of its unrivaled security and privacy. You can find legitimate products such as basketball shoes, apparel, research papers, and other items on the dark web. Of course, you can also find plenty of illegal items such as hacked streaming media accounts, stolen personal identifiable information, credit card account numbers, firearms, and drugs, too. The default Tor search engine is a dark version of DuckDuckGo, but there are other dark web search engines you can use on Tor.

Whonix OS: Advanced Security Through Isolation
Tails also protects you from possible malware, viruses, or keystroke loggers that may have already infected the computer, as it doesn’t run the operating system already installed on the device. While this is good advice for any type of web browsing, be particularly careful not to offer up any personal details, such as your credit card info or email address. Use cryptocurrency to buy anything, and use a disposable email address for any type of communication on the dark web. Government cyber teams can take such websites down, arrest the owners and then use the website to track and follow users that show activity on the website. On top of that, the installation process of Freenet is rather easy.
Finding Onion Sites
Think of it as a whole separate operating system, complete with apps and files, that runs entirely on removable media. Dark Web also does not have traditional websites like you find on the Surface web. By traditional websites, we mean websites with domains like .com, .org, .gov, etc., and easy-to-remember names, like google.com.
How To Install Tor
He previously reported from Colombia for four years, where he wrote travel guidebooks to Latin America, and speaks Spanish fluently with a hilarious gringo-Colombian accent. He holds a Masters degree in Information and Cybersecurity (MICS) from UC Berkeley. Such hacking techniques ought to concern everyone, as innocent Tor users will inevitably get caught up in such fishing expeditions. The most successful technique to de-anonymize Tor Browser users has been to hack them.
Alternatively, bridges can be obtained through other channels, such as sending an email to the Tor Project’s bridge distribution service or via a dedicated Telegram channel. Once obtained, these bridge addresses can be manually entered into the Tor Browser’s configuration. Another circumvention tool integrated into Tor Browser is “Snowflake,” which allows users to connect through temporary, ephemeral proxies, further aiding in bypassing network blocks. The choice of which circumvention method to use often depends on the specific nature of the blocking being encountered.
Where To Download Tor Browser
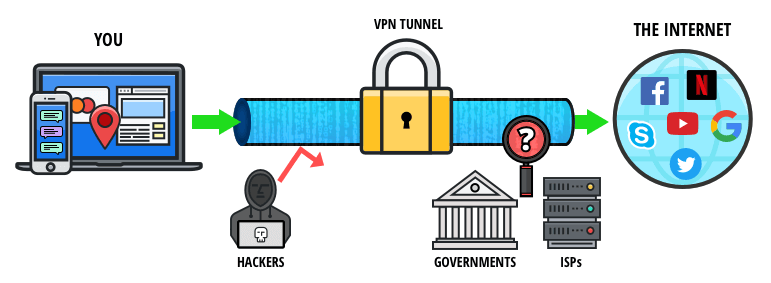
Firstly, it could jeopardize your anonymity if you submit any kind of personal information during a dark web browsing session. Secondly, there are many malicious, fake, and phishing sites on the dark web, which might look like sites you trust but are actually designed to steal your data. However, note that a VPN is not a definitive or comprehensive form of protection.
What Is The Dark Internet?
A VPN app opens another potential vulnerability, as it can log the sites you visit via Tor. If you must use one, ensure it’s a VPN with a strict, independently audited no-logs policy. It encrypts data during transmission to avoid the risk of being eavesdropped.
With rising curiosity around hidden corners of the internet, many professionals wonder, “how to access the dark web” safely. From cybersecurity researchers to IT managers, understanding how to navigate the dark web can help monitor cyber threats, protect sensitive data, and investigate cybersecurity incidents. The technology behind this anonymous connection is known as “onion routing,” which utilizes a layered approach to obscure data and protect users’ locations on the network. Then there’s the less popular VPN over Tor, which is advised against by the official Tor Project. Only two VPN providers that we know of, AirVPN and BolehVPN, offer this service, although neither of these score highly for speeds.
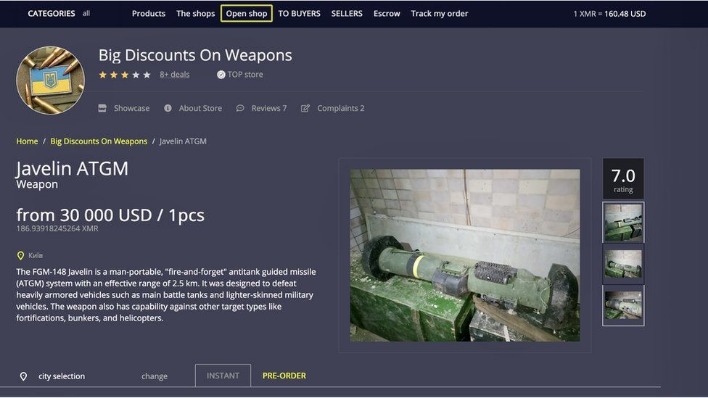
Some .onion dark websites are known to contain malware, and dangerous scripts designed to damage your computer, steal your information and identify you. Although the dark web represents a small fraction of the totality of the deep web, it has attracted perpetual media attention over the last few years. You need a special browser to access it, and when you do, your internet traffic is not wired through the network of interrelated public servers in the way it is when you access the surface web.
Step 2: Download Tor Browser
If we have made an error or published misleading information, we will correct or clarify the article. If you see inaccuracies in our content, please report the mistake via this form. If you manage to not expose your private information and avoid illicit activities, you can be sure everything will be okay. This internet space can be dangerous but you can safely get on it by using a VPN and then connecting to Tor. Our experience has shown that this is the #1 way of doing things without risking your privacy.
Onion sites are hosted on the Tor network, enabling them to share information without revealing users’ IP addresses. They facilitate secure communication over the web and protect from third-party surveillance. Regular browsers can’t open Onion sites because they aren’t part of the standard domain name system.
Using the Tor browser is simple, but knowing when to fire it up is more complicated. Another challenge is CAPTCHAs; because Tor behaves differently than other browsers, it’s more likely to trigger the bot-hunting system, so be prepared to face more of them than usual. Launch the Tor Browser from your desktop or Start menu, then click Connect on the welcome screen to establish a secure connection to the Tor network. Install Norton VPN to help you access content and safeguard the data you share. Tor doesn’t provide you with links to start surfing the Dark Web, so it’s up to you to find them instead. In fact, you’re probably very often within the Deep Web and you don’t even know it.
These sites often contain material that is not allowed on the “clearweb” of public sites. Depending on what you intend to do on the Dark Web, some users recommend placing tape over your laptop’s webcam to prevent prying eyes watching you. If you’re reading in the hope of finding out about torrent files, check out our separate guide on how to use torrent sites in the UK. Go to and download the Tor Browser Bundle, which contains all the required tools. Run the downloaded file, choose an extraction location, then open the folder and click Start Tor Browser. For example we have a ‘staging’ version of this very website that is blocked from being indexed by search engines, so we can check stories before we set them live.
- It is perhaps the most secure way to run applications anonymously.
- Repeat this process until you get an IP address from your desired country.
- MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice.
- This feature offers a more direct and potentially more trustworthy way to find the onion versions of legitimate websites.
- Once you’re in, continue to use caution to protect your anonymity and safety.
For the most security-conscious, you can even install the Tails operating system on a flash drive and run Tor from that. The last node (exit node), through which Tor routes your traffic, is delicate. In rare cases, attackers can exploit an unsecure node to monitor Tor users or gain unauthorized access to accounts. Always verify a site’s legitimacy before visiting – onion addresses are long, random strings, making it easier for malicious actors to create lookalike addresses for phishing. A little typo can lead you to a clone designed to trick users into handing over sensitive data.



