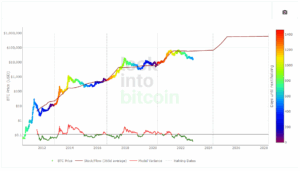
The classification is performed in five steps (see Fig. 1), as detailed next. Additionally, we analyse the U2U...
Uncategorized
The decentralized nature of crypto complicates enforcement, prompting governments to develop advanced tracking strategies. Emerging threats include...
In this example, we’re going to run through the steps for purchasing CBD oil off the darknet,...
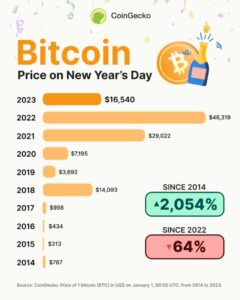
This approach showed instances where prices in fiat increased but simultaneously decreased when priced in Bitcoin. This...
Due to its extensive inventory and reputation for reliability, Brian’s Club has maintained a significant presence on...
Similarly, there is no unique choice for the classification parameters or ground truth for fitting them. In...
Unlike VPNs, which also provide anonymity, it reroutes the users’ traffic through a network of nodes rather...
Buyers and sellers used wallets controlled either directly or through third-party mixers and exchanges. Vendors on Incognito...
They’d secretly been running Hansa for a few weeks, harvesting user data and hijacking the site’s inbuilt...
{The best month for the darkweb market was this June, when the value of brokered sales peaked...